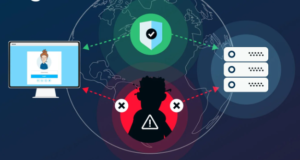
Understanding Man-in-the-Middle (MitM) Attacks
Introduction In today’s interconnected digital landscape, ensuring the security and privacy of online communications is paramount. One of the most pervasive and dangerous threats to these communications is the Man-in-the-Middle (MitM) attack. This form of cyberattack allows an adversary to intercept, modify, or eavesdrop on communication between two parties without their knowledge. Whether it’s stealing … Continue reading Understanding Man-in-the-Middle (MitM) Attacks
0 Comments